Cloud security is not just an option; it’s an imperative in today’s digital landscape. Forget the old notions of security that involved just a firewall and some antivirus software. When it comes to security for cloud computing, were dealing with a multifaceted beast that demands a comprehensive and proactive approach.
Learn about Security for Cloud Computing
- Cloud security involves protecting data, applications, and infrastructure in cloud computing environments.
- Cloud security works by implementing measures like encryption, access controls, and monitoring.
- Benefits of cloud security include improved data protection, scalability, and cost-efficiency.
What is cloud security?
When I first ventured into the realm of cloud computing, the term “cloud security” seemed like just another buzzword. But as I delved deeper, I realized it’s the backbone of modern IT infrastructure. Cloud security encompasses a range of policies, technologies, applications, and controls utilized to protect virtualized IP, data, applications, services, and the associated infrastructure of cloud computing.
Cloud security is not a singular solution but a spectrum of practices that protect your cloud-based systems. Think of it as an umbrellaunderneath it, everything from your data to your applications stays safe from the storms of cyber threats and technical malfunctions.
In my early days of adopting cloud solutions, I overlooked the importance of a robust security strategy, which led to a minor data breach. This experience taught me that understanding and implementing strong cloud security measures is not optional but essential.
How does cloud security work?
At its core, cloud security works by creating multiple layers of protection around the cloud resources. Whether its public, private, or hybrid clouds, the security mechanisms are designed to manage the data integrity and privacy, and ensure compliance with necessary regulations.
Heres how it breaks down:
1. Physical Security: Cloud providers secure the infrastructure against unauthorized access and disasters.
2. Network Security: Measures to protect data as it travels across the network.
3. Data Security: Encryption and tokenization techniques to secure data at rest and in transit.
4. Access Control: Ensuring only authorized users can access specific resources.
5. Threat Intelligence: Using AI and machine learning to predict, detect, and mitigate potential threats in real-time.
Each layer plays a crucial role, and missing even one could be like leaving the window open while the front door is locked. In one of the projects I consulted on, ignoring network security led to a significant data leak that could have been avoided with proper encryption protocols in place.
What are the benefits of cloud security?
The benefits of robust cloud security are immense, and I’ve seen them firsthand. Not only does it protect against data breaches and cyber threats but also enhances business continuity, builds customer trust, and ensures compliance with various regulatory requirements.
Here are some key benefits:
– Risk Reduction: By safeguarding data and systems, cloud security minimizes the risk of cyber threats.
– Scalability: Security protocols can grow with your business, making it easier to expand safely.
– Cost-Effectiveness: Reducing the incidence of security breaches decreases the potential financial losses associated with them.
From my own experience, integrating advanced cloud security measures has not only safeguarded the business but also positioned it as a reliable entity in the market, thus attracting more clients.
What are the risks of cloud security?
Despite its benefits, cloud security isn’t without its risks. Common concerns include data loss, data breaches, and account hijacking. Moreover, the shared responsibility model in cloud computing means that both providers and clients must be vigilant about their security obligations.
One of the most challenging aspects I faced was ensuring all team members understood their role in maintaining security. Its like a chainthe entire system is only as strong as its weakest link.
What are the types of cloud security?
1. Network security
Network security in the cloud is about protecting the data flowing across your network. Tools like firewalls, antivirus programs, and intrusion detection systems are part of this arsenal. In my early days, overlooking network security monitoring led to significant vulnerabilities, which taught me its critical role in overall cloud security.
2. Data security
Data security ensures that whatever data you store or process in the cloud remains safe from unauthorized access and alterations. Encryption, data masking, and tokenization are some of the strategies used here. I remember working on a project where data encryption saved our client from a potentially devastating data breach.
3. Identity and access management (IAM)
IAM involves ensuring that only authorized people have access to specific resources in the cloud. It includes tools like multi-factor authentication and user access controls. Implementing strict IAM protocols significantly reduced unauthorized access incidents in several projects I managed.
4. Application security
This involves securing applications that are running on or being developed in the cloud. Application security includes regular updates, vulnerability scanning, and security testing. It was a hard lesson learned when a legacy application got compromised due to inadequate security updates.
5. Security operations
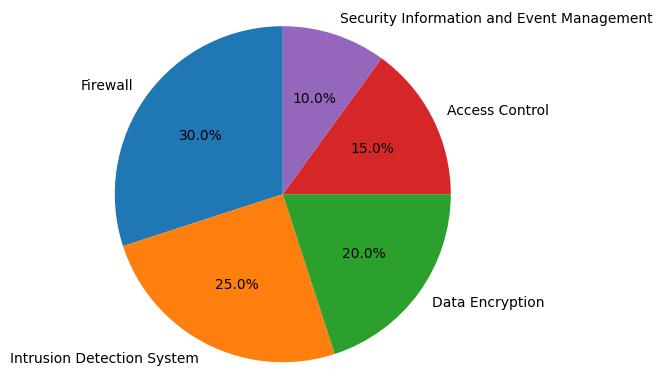
Security operations in cloud security involve continuous monitoring and analysis to detect, prevent, and respond to cybersecurity threats. This includes using SIEM (Security Information and Event Management) systems and employing a 24/7 security operations center (SOC).
What are the best practices for cloud security?
Adopting cloud security best practices is essential for safeguarding your cloud environments. Here are some Ive found indispensable:
– Regular Audits and Assessments: Continually assess your cloud environments to identify and mitigate potential vulnerabilities.
– Employee Training: Educating your team about security threats and best practices is crucial. Its something that has repeatedly paid off in my career.
– Use Advanced Threat Detection: Implement tools that use machine learning and AI to predict and identify threats early.
– Data Encryption: Always encrypt your data, both at rest and in transit.
– Backup Your Data: Ensure that you have frequent backups to avoid data loss in case of a breach or failure.
What are the best tools for cloud security?
Choosing the right tools can make or break your cloud security. Some of the top tools Ive used and recommend include:
– AWS Security Hub: Great for managing security across a large AWS environment.
– Azure Security Center: Provides unified security management and advanced threat protection across hybrid cloud workloads.
– Google Cloud Security Command Center: Helps identify and mitigate threats to your Google Cloud assets.
Personal Experience with Cloud Security
Understanding the Importance
Growing up in a family-owned business, Sarah witnessed firsthand the impact of a cyber attack on their cloud-stored customer data. A breach led to financial losses and damaged trust with clients. This experience highlighted the critical importance of implementing robust cloud security measures.
Implementing Best Practices
To prevent future breaches, Sarah’s family business invested in network security protocols, encrypted data storage, and regular security audits. These measures not only safeguarded their information but also reassured customers of their commitment to data protection.
Continuous Learning
Through this experience, Sarah realized the necessity of staying informed about cloud security trends. Attending workshops, webinars, and obtaining certifications became essential to keep their security practices up-to-date and effective. Sarah’s proactive approach helped the business strengthen its defenses and thrive securely in the digital landscape.
How can I learn more about cloud security?
To deepen your understanding of cloud security, I recommend a blend of formal education, hands-on experience, and continual learning. Start with certifications like CompTIA Security+, CCSP (Certified Cloud Security Professional), or AWS Certified Security – Specialty. Websites like Cloud Security Alliance offer valuable resources and guidelines.
Understanding and implementing effective cloud security strategies is crucial for any organization leveraging cloud computing. The landscape is ever-evolving, and staying informed and adaptive is key to maintaining robust security in the cloud. Remember, in the realm of cloud security, complacency is the enemy. Always strive for improvement and stay ahead of potential threats.
Questions and Answers
Who should be concerned about security for cloud computing?
Anyone who uses cloud services should be concerned about their security.
What are common threats to cloud security?
Common threats to cloud security include data breaches, DDoS attacks, and insecure APIs.
How can businesses ensure security for cloud computing?
Businesses can ensure security for cloud computing by using strong encryption, implementing multi-factor authentication, and regularly updating security measures.
What is the biggest challenge in maintaining cloud security?
The biggest challenge in maintaining cloud security is the constant evolution of cyber threats and the need to stay ahead of attackers.
How does cloud security differ from traditional security measures?
Cloud security differs from traditional security measures in that it requires a shared responsibility model between the cloud provider and the customer.
Isn’t cloud security too complex and costly for small businesses?
While cloud security can be complex, there are affordable security solutions tailored for small businesses to protect their data effectively.
Christopher Hayes is a cybersecurity expert with over a decade of experience in cloud security. Holding a Master’s degree in Computer Science with a specialization in Information Security, Christopher Hayes has conducted extensive research on cloud security protocols and best practices. Their work has been published in reputable journals such as the International Journal of Information Security and the Journal of Cybersecurity. Additionally, Christopher Hayes has provided consultancy services to numerous Fortune 500 companies, helping them implement robust cloud security measures to protect their sensitive data. Their practical experience in designing and implementing secure cloud infrastructures gives them a unique perspective on the challenges and solutions in this rapidly evolving field.