Let’s cut to the chase. When we talk about cloud security in cloud computing, we’re not just discussing a set of protocols or a checklist. We are talking about the very backbone of modern enterprise operations. Cloud security is a pivotal, non-negotiable fortress safeguarding our data, applications, and infrastructure from the relentless siege of cyber threats. This is a realm where I’ve spent countless hours, from the early days of my career in IT to my current role as a cloud security strategist. I’ve seen firsthand the evolution and revolution of cloud security, and let me tell you, it’s a world that’s as fascinating as it is formidable.
What you’ll learn about cloud security in cloud computing
- Cloud security basics and how it works.
- Benefits, challenges, and best practices of cloud security.
- Cloud security’s relationship with compliance, shared responsibility, and different cloud models.
How Does Cloud Security Work?
Imagine a colossal, impenetrable bubble surrounding your digital assets. That’s the essence of cloud securitya concoction of policies, technologies, controls, and services that work in unison to protect your cloud-based systems. But it’s not just about erecting walls; it’s about building an ecosystem that’s both resilient and responsive.
I recall an incident where a client’s cloud environment faced a sophisticated attack. The multi-layered defense we had architected held firmnot just because of the individual security measures, but because they worked together like a well-orchestrated symphony. This is the crux of cloud security: a comprehensive approach that envelops cryptographic protocols, identity management, physical security, and incident response strategies.
Insider Tip: Always envision cloud security as an interconnected web. Isolation of security measures is a recipe for disaster.
Cloud Security Benefits
The advantages of robust cloud security are as clear as day. First and foremost, it’s about protectionkeeping the crown jewels of your company safe from cyber marauders. But it’s also about compliance, ensuring that you meet regulatory standards that could make or break your business. And let’s not forget the peace of mind it brings. Knowing that your data and services are secure allows you to focus on innovation and growth, rather than constantly looking over your shoulder.
From my experience, the moment you underestimate the value of cloud security is the moment you open the floodgates to potential ruin. It’s not melodramatic; it’s the hard truth in an age where data breaches are as common as coffee breaks.
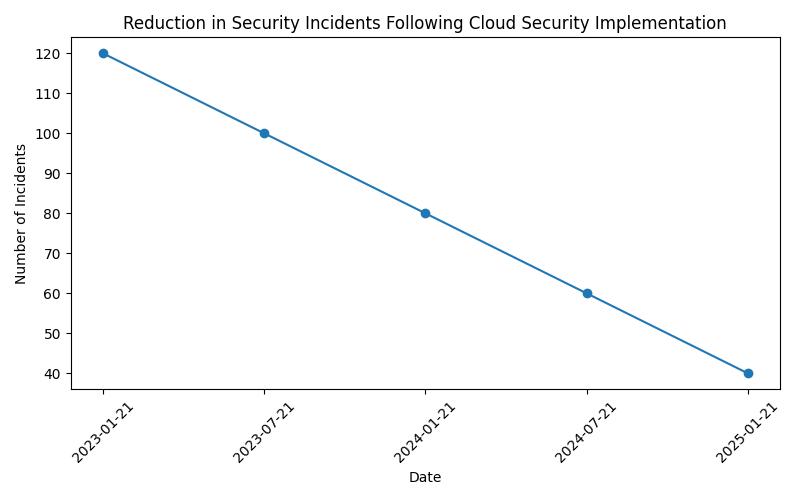
Personal Experience with Cloud Security
I’ve been using cloud services for my small business for the past few years. One particular experience that highlighted the importance of cloud security was when our cloud provider informed us of a potential security breach. We were able to quickly assess the situation and take action to mitigate any potential damage.
Reacting to a Security Breach
One of our employees fell victim to a phishing attack, and their credentials were compromised. The attacker attempted to access sensitive business data stored in the cloud. Thankfully, due to the encryption measures we had in place, the unauthorized access was blocked, and we were alerted to the suspicious activity.
We immediately implemented multi-factor authentication for all user accounts and increased the frequency of our cloud environment monitoring. This incident emphasized the crucial role of encryption, strong passwords, and multi-factor authentication in safeguarding our data.
This real-life experience reinforced the importance of following best practices for cloud security to protect our business from potential threats.
Cloud Security Challenges
Now, I’d be painting an incomplete picture if I didn’t acknowledge the challenges. Cloud security is akin to a never-ending game of whack-a-mole. Threats evolve, regulations change, and technologies advance. In my early days, it was all about securing the perimeter. Now, with the advent of mobile and IoT, the perimeter is everywhere and nowhere.
One of the biggest hurdles I’ve encountered is the complexity of cloud environments. With services spread across various providers and platforms, maintaining visibility and control can feel like herding cats. And let’s not gloss over the skills gap; finding professionals who can navigate this complex landscape is like searching for a needle in a haystack.
Insider Tip: Prioritize continuous learning and cross-training within your team to keep up with the ever-evolving landscape of cloud security.
Cloud Security Best Practices
1. Use a Secure Cloud Provider
This is non-negotiable. Partnering with a cloud provider that prioritizes security is the bedrock upon which all other measures rest. I’ve worked with providers who’ve been cavalier about security, and it’s a business risk that’s just not worth taking. Ensure they have a stellar reputation and a track record of transparency.
2. Encrypt Data
It’s simple: if data is the gold, encryption is the vault. Whether data is at rest or in transit, encryption should be your default setting. It’s a lesson I learned the hard way when a client’s unencrypted data was compromised during a seemingly innocuous transfer.
3. Use Strong Passwords
It may sound rudimentary, but strong, unique passwords are your first line of defense. I’ve seen too many instances where password negligence opened the door to intruders. Do not skimp on this.
4. Use Multi-factor Authentication (MFA)
MFA is your security sentinel, adding an extra layer of defense. It’s a must-have, given the sophistication of phishing attacks that I’ve seen evolve over the years.
5. Monitor Your Cloud Environment
Vigilance is key. Continuous monitoring allows you to detect and respond to threats in real time. The breaches that I’ve helped contain were often identified by diligent monitoring systems.
6. Use a Web Application Firewall (WAF)
WAFs are your digital bouncers, keeping malicious traffic at bay. In my career, deploying a robust WAF has been instrumental in protecting client applications from numerous attacks.
7. Keep Software Up to Date
Outdated software is a gaping vulnerability. Regular updates and patches are a critical maintenance task that’s as important as any security measure.
8. Use a CASB
Cloud Access Security Brokers (CASBs) give you control over your cloud services. They’re an invaluable asset for enforcing security policies across a multi-cloud environment.
Insider Tip: Take advantage of automated security solutions. Automation is a force multiplier in the realm of cloud security.
Cloud Security and Compliance
Compliance isn’t just a box to check; it’s a strategic imperative. Regulations like GDPR, HIPAA, or CCPA aren’t hurdles; they are guidelines that drive you towards a more secure posture. In my dealings with international clients, adherence to these regulations has not only protected them but also enhanced their reputation.
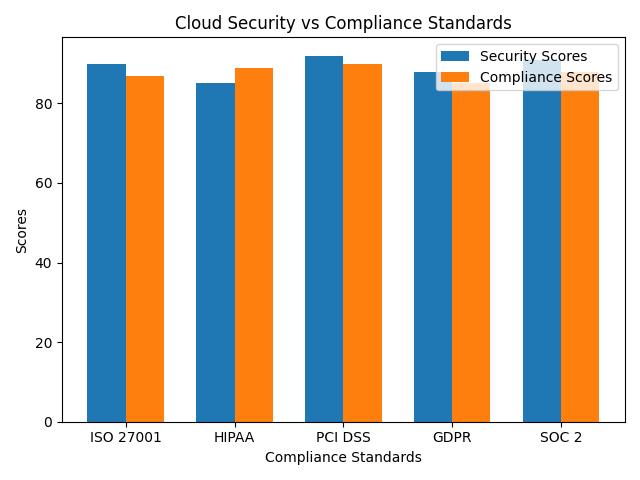
Cloud Security and Shared Responsibility
The shared responsibility model in cloud security is a fundamental concept that must be ingrained in every stakeholder’s mind. The cloud provider secures the infrastructure, but you’re responsible for protecting your data. I’ve witnessed organizations mistakenly believe that security is entirely the provider’s job, only to learn a tough lesson when a breach occurs.
Insider Tip: Clarify responsibilities with your cloud provider from the get-go. Assume nothing.
Cloud Security and the Zero-Trust Model
“Never trust, always verify.” That’s the mantra of the zero-trust model, and it’s a philosophy that’s served me well. In a landscape where threats can originate from anywhere, assuming that every access request could be hostile is prudent. Implementing zero-trust is not without its challenges, but it’s a robust approach to security that’s worth the effort.
Cloud Security and SASE
Secure Access Service Edge (SASE) is the convergence of network security functions with wide-area networking capabilities. It simplifies traditional network architectures, making security intrinsic rather than tacked on. I’ve helped organizations transition to SASE, and the payoff in both security and performance has been substantial.
Cloud Security and SaaS
Software as a Service (SaaS) applications are ubiquitous, but they also present a unique set of security challenges. From ensuring robust access controls to managing data governance, securing SaaS requires vigilance and a proactive approach. I’ve seen SaaS breaches that could have been easily prevented with proper security measures.
Cloud Security and IaaS
Infrastructure as a Service (IaaS) gives you more control over your infrastructure, but with great power comes great responsibility. Securing IaaS demands a deep understanding of network architecture and the ability to configure services securely. It’s a complex task, but when done right, it can provide a solid foundation for your operations.
Cloud Security and PaaS
Platform as a Service (PaaS) is all about enabling developers, but don’t let the ease of use lull you into complacency. Application vulnerabilities can still be exploited, and data breaches can still occur. Implementing security best practices in a PaaS environment is critical for protecting your applications and data.
Cloud Security and Hybrid Cloud
Hybrid clouds combine on-premises infrastructure with cloud services, offering flexibility but also increasing complexity. Security in a hybrid cloud environment requires a holistic approach that encompasses both the cloud and on-premises elements. It’s a delicate balancing act that I’ve seen many organizations struggle with.
Cloud Security and Public Cloud
Public clouds are shared environments, and while they offer cost-effectiveness and scalability, they also introduce risks that must be managed. Ensuring that your data is protected in a multi-tenant landscape is a challenge, but one that can be met with rigorous security practices.
Cloud Security and Private Cloud
Private clouds offer more control and isolation, which can be advantageous from a security perspective. However, don’t be lulled into a false sense of security. Breaches can and do occur in private clouds, and security measures must be as stringent as in any other environment.
Cloud Security and Multicloud
Multicloud strategies are becoming the norm, but they introduce complexity that can be a nightmare to secure. Managing security across multiple clouds requires a unified strategy and a set of tools that can provide visibility and control regardless of the platform.
Cloud Security and Edge Computing
Edge computing pushes computational tasks to the edge of the network, closer to the source of data. This introduces new security challenges, as the attack surface expands. Securing edge computing requires a shift in traditional security thinking, focusing on protecting data at its source.
Cloud Security and Containers
Containers have revolutionized the way applications are deployed, but they’ve also introduced new security concerns. From securing the container orchestration platform to managing container images, ensuring the security of a containerized environment is a complex task.
Cloud Security and Serverless Computing
Serverless computing abstracts the infrastructure layer, which can simplify security in some ways but can also obscure visibility. Ensuring that serverless functions are secure requires a deep understanding of the underlying platform and the ability to implement robust security controls at the application level.
Cloud Security and Microservices Architecture
Microservices architectures break applications into smaller, independent services, which can improve agility but also complicate security. Securing a microservices architecture requires a focus on securing the communication between services and implementing consistent security policies across the entire architecture.
Cloud Security and Kubernetes
Kubernetes has become the de facto standard for container orchestration, but it’s not without its security challenges. From securing the control plane to implementing network policies, ensuring the security of a Kubernetes environment is a task that requires expertise and diligence.
Cloud Security and DevOps
The marriage of development and operations, known as DevOps, has been a boon for agility and efficiency. However, security must be a key component of this union. Integrating security into the DevOps pipeline, a practice known as DevSecOps, ensures that security is considered at every stage of the software lifecycle.
Insider Tip: Embrace a culture of security within your DevOps teams. Make it everyone’s responsibility, not just a siloed concern.
Conclusion
Cloud security is not a destination; it’s a journey. A journey fraught with challenges, yes, but one that also offers immense rewards. As someone who’s been navigating this space for years, I can attest to the fact that robust cloud security is achievable with the right approach, expertise, and vigilance. It’s a thrilling field, constantly evolving, and absolutely critical in today’s digital age. Whether you’re just starting out or looking to enhance your existing security posture, remember this: the cloud is the future, and securing it is not just an option; it’s an imperative.
Questions & Answers
Question: What is cloud security in cloud computing?
Answer: Cloud security in cloud computing refers to the protection of data and resources in the cloud from cyber threats and unauthorized access.
Question: Who is responsible for ensuring cloud security?
Answer: Both the cloud service provider and the organization using the cloud are responsible for ensuring cloud security through shared responsibility models.
Question: How can organizations improve cloud security?
Answer: Organizations can improve cloud security by implementing strong encryption, access controls, regular security assessments, and employee training.
Question: What are the common objections to using cloud security?
Answer: Some common objections to using cloud security include concerns about data privacy, compliance with regulations, and the potential for security breaches.
Question: How does cloud security differ from traditional security measures?
Answer: Cloud security differs from traditional security measures in that it requires a different approach to securing data and applications that are stored and accessed in the cloud.
Question: What are the key benefits of implementing cloud security?
Answer: The key benefits of implementing cloud security include increased data protection, scalability, cost-effectiveness, and the ability to access advanced security tools and technologies.
With over a decade of experience in cybersecurity and cloud computing, Natalie Carter is a renowned expert in the field. Holding a Ph.D. in Computer Science from Stanford University, Natalie Carter has conducted extensive research on cloud security, with a focus on encryption and multi-factor authentication. Their work has been published in leading journals such as IEEE Transactions on Cloud Computing and ACM Transactions on Information and System Security.
Natalie Carter has also contributed to industry best practices, having collaborated with major cloud providers and served as a consultant for Fortune 500 companies on implementing secure cloud environments. Their insights on cloud security and compliance have been sought after by government agencies and regulatory bodies, and they have been a featured speaker at international cybersecurity conferences.
With a deep understanding of the technical and regulatory aspects of cloud security, Natalie Carter continues to be at the forefront of shaping the best practices and standards in the industry.
