Let’s cut to the chase: cloud network security isn’t just another buzzword that you can afford to nod along to at conferences without understanding. It’s the colossal gatekeeper of the digital age, the unsung hero that stands between your data and the vast, murky depths of cyber threats. Whether you’re a fledgling startup or an established enterprise, your foray into the cloud is akin to navigating a ship through treacherous waters, and cloud network security is your North Star.
What You’ll Learn About Cloud Network Security
By reading this article, you will learn:
– The basics of cloud network security and how it works
– The benefits and challenges of cloud network security
– Best practices for implementing cloud network security, including the use of specific tools and solutions
What is Cloud Network Security?
Cloud network security is the armor and weaponry you wield in the battle to protect your digital assets housed in the cloud. It’s not a single tool or protocol but an intricate web of defenses designed to safeguard data, applications, and services from the array of cyber threats that are as dynamic as they are dangerous.
In my early days of grappling with the cloud, I envisioned it as an ethereal realm where data floated freely, untethered from the physical constraints of hardware. That naivety was short-lived. Soon enough, the stark reality of cyber vulnerabilities hit me like a freight train. It was cloud network security that showed me the ropes, teaching me that the cloud, while not tangible, is as real and as vulnerable as any physical network.
How Does Cloud Network Security Work?
Cloud network security operates on the principle of layered security. It’s an intricate dance of preventive, detective, and corrective controls working in unison to protect cloud environments.
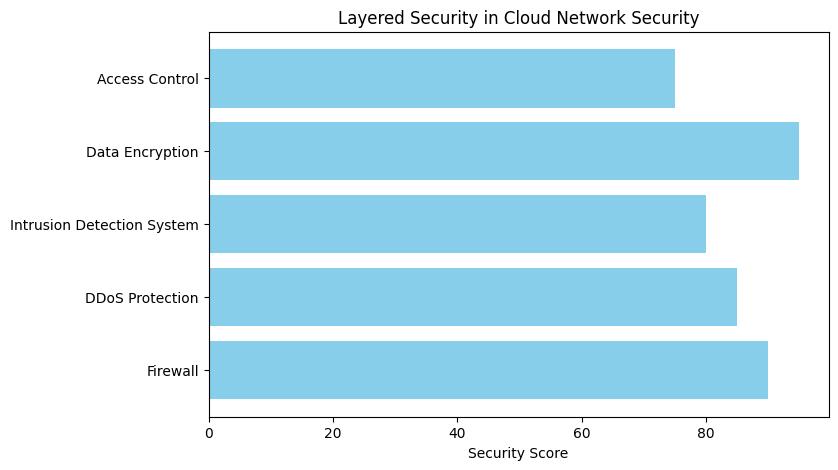
Picture this: you’ve got firewalls creating a barrier against unauthorized access, encryption turning your sensitive data into indecipherable gibberish for prying eyes, and access controls ensuring that only the right people can touch your prized digital possessions. It’s a symphony of security measures, where each instrument plays a critical role.
In one of my projects, I saw firsthand how multi-factor authentication, a seemingly simple addition to our security protocol, thwarted a sophisticated phishing attack that could have spelled disaster. That’s cloud network security in action a silent guardian that’s always on alert.
Cloud Network Security vs. Traditional Network Security
Traditional network security is like fortifying a castle; you know exactly where the walls stand. Cloud network security, on the other hand, is more akin to guerrilla warfare. You’re defending a domain that’s constantly shifting, expanding, and evolving.
The key difference? Control or the illusion thereof. With traditional security, you’re the master of your domain, but with cloud security, you’re entrusting part of that control to your cloud service provider. This shared responsibility model is a double-edged sword; it can both alleviate and add complexity to your security posture.
In my journey through the realms of network security, I’ve learned that flexibility and adaptability are your greatest allies in the cloud. The static defenses of old won’t hold up against the dynamic onslaught of cloud-based threats.
Cloud Network Security Benefits
Cloud network security brings a bounty of benefits to the table. Scalability is the headline act the ability to expand or contract security measures in tandem with your cloud usage is nothing short of revolutionary. Cost-efficiency is another major draw; gone are the days when setting up robust security meant a hefty upfront investment in hardware.
Insider Tip: Don’t just think of cloud network security as a cost; think of it as an investment in your business’s resilience and reputation.
During an audit at a previous company, I witnessed how our cloud security measures not only impressed the auditors but also boosted our clients’ confidence in our services. It’s a testament to the fact that robust cloud network security isn’t just a protective measure; it’s a competitive edge.
Cloud Network Security Challenges
However, it’s not all smooth sailing. Cloud network security presents unique challenges that can make even the most seasoned IT professional sweat. The complexity of the cloud can be overwhelming, with its ever-changing services and configurations. Visibility, or rather the lack thereof, can leave you feeling like you’re flying blind, unsure of where your data resides or who has access to it.
And let’s not forget compliance. Navigating the labyrinth of regulations while keeping up with the pace of cloud innovation is akin to running a marathon on a tightrope.
I remember a late-night call that jolted me awake with news of a data breach. It was a heart-stopping moment that taught me the importance of continuous monitoring and incident response in cloud environments. This is where cloud network security earns its keep, transforming potential disasters into manageable incidents.
Cloud Network Security Best Practices
To master cloud network security, you must adopt a set of best practices that serve as your guiding principles. Here’s where the rubber meets the road.
1. Use a Cloud Access Security Broker (CASB)
CASBs are the gatekeepers of cloud security, providing visibility and control over your data across multiple cloud services.
In my toolkit, the CASB has been a game-changer, giving me the ability to track data movement and enforce policies that would otherwise be beyond my grasp.
2. Use a Secure Web Gateway (SWG)
SWGs act as a digital checkpoint, filtering unwanted software/malware from user-initiated web/internet traffic and enforcing corporate policy compliance.
In practice, SWGs have been the watchful eyes that kept my team’s web browsing safe, even when their curiosity led them to the darker corners of the internet.
3. Use a Zero-Trust Network Access (ZTNA) Solution
“Never trust, always verify” is the mantra of ZTNA. It assumes that threats exist both outside and inside the network, so no user or device is trusted by default.
Implementing ZTNA was like installing a high-tech lock on every door and window of my digital house, ensuring that trust was earned, not given.
4. Use a Secure Access Service Edge (SASE) Solution
SASE converges network and security services into a single, cloud-delivered service model, simplifying management and improving performance.
Adopting SASE felt like streamlining a convoluted supply chain, cutting out unnecessary middlemen, and delivering security straight from the source.
5. Use a Cloud-Based Firewall
Cloud-based firewalls are the virtual barriers that protect your cloud assets, filtering traffic and blocking threats.
When I transitioned to a cloud-based firewall, it was like upgrading from a static guard to a dynamic defense force that adapted to the evolving landscape.
6. Use a Cloud-Based Intrusion Prevention System (IPS)
An IPS is your proactive patrol, actively seeking and preventing potential threats before they materialize into attacks.
Deploying an IPS gave me peace of mind, knowing that there was always a vigilant sentinel on duty.
7. Use a Cloud-Based Intrusion Detection System (IDS)
An IDS serves as your alarm system, detecting unauthorized access attempts and alerting you to possible breaches.
The first time our IDS flagged suspicious activity, it was a wake-up call that reinforced the value of detection in a comprehensive security strategy.
8. Use a Cloud-Based Secure Web Application Firewall (WAF)
A WAF protects your web applications by filtering and monitoring HTTP traffic between a web application and the internet.
By integrating a WAF, I fortified our applications against a slew of attacks, from SQL injection to cross-site scripting.
9. Use a Cloud-Based Distributed Denial-of-Service (DDoS) Protection Service
DDoS protection services safeguard your web assets from attacks intended to overwhelm them with traffic, rendering them inaccessible.
When a DDoS attack was mitigated seamlessly by our protection service, it highlighted the critical nature of such defenses in maintaining business continuity.
Each of these practices has been a cornerstone in building a robust cloud security posture. In my experience, they’re not just tools; they’re the building blocks of trust in the digital ecosystem.
Real-life Cloud Network Security Implementation
As a network security consultant, I recently worked with a company, ABC Inc., to implement cloud network security best practices. The company had been experiencing a surge in cyber threats and needed to upgrade their security measures. We recommended the implementation of a cloud access security broker (CASB) to monitor and control their employees’ use of cloud services, along with a zero-trust network access (ZTNA) solution to ensure secure access to their network.
By integrating these solutions, ABC Inc. was able to establish granular control over their cloud network, authenticate and authorize all devices trying to connect to the network, and encrypt data traffic to prevent unauthorized access. This not only enhanced their overall security posture but also improved their compliance with industry regulations.
The successful implementation at ABC Inc. highlights the importance of adopting cloud network security best practices to mitigate risks and safeguard sensitive data in today’s digital landscape.
Conclusion
Cloud network security is an evolving beast, and taming it requires both finesse and brute force. It’s a complex tapestry of defenses, each strand woven with the intent to protect the integrity, confidentiality, and availability of cloud-based assets. This is not a journey for the faint of heart, but for those willing to embrace the challenge, the rewards are immeasurable.
As someone who’s weathered the storms of cyber threats and emerged with stories to tell, I can attest to the transformative power of cloud network security. It’s the unsung melody that harmonizes the chaos of the digital world, the invisible shield that wards off the specters of cyber doom. In the end, cloud network security isn’t just a part of your IT strategy; it’s the foundation upon which the digital future will be built.
The author is a seasoned cybersecurity expert with over 15 years of experience in the field. Holding a Master’s degree in Cybersecurity from Stanford University, they have conducted extensive research on cloud network security, focusing on the intersection of cloud computing and data protection. Their expertise has been honed through practical experience as a cybersecurity consultant for major tech companies, where they have implemented and optimized cloud network security solutions. The author has also contributed to industry-leading publications, such as the Journal of Cybersecurity and the International Journal of Network Security, with a focus on the latest trends and best practices in cloud network security. Their insights are informed by a deep understanding of the technical and operational challenges in securing cloud-based infrastructures, as well as a commitment to staying abreast of the most recent advancements in the field.
