Cloud security is not merely a buzzword; it’s a pivotal aspect of modern IT infrastructure that influences everything from individual privacy to national security. While many organizations rush to leverage cloud technology for its scalability and cost-effectiveness, few grasp the full spectrum of security implications that come with it. Lets dive into the expansive world of cloud IT security and explore why its more than just a necessityit’s a strategic imperative.
Understanding Cloud IT Security
Learn the essentials of cloud IT security, including its significance, challenges, best practices, and tools. – What is cloud security? It refers to the set of policies, controls, and technologies designed to protect data, applications, and infrastructure associated with cloud computing. – Why is cloud security important? It is crucial for safeguarding sensitive information, ensuring compliance, and maintaining customer trust in cloud services. – What are the key cloud security challenges? Challenges include data breaches, compliance issues, and managing third-party risks, which are vital for organizations to address.
What is Cloud Security?
Cloud security refers to a broad set of policies, technologies, and controls that work in unison to protect data, applications, and the entire infrastructure related to cloud computing. Unlike traditional security models, cloud security needs to be dynamic and adaptable to accommodate the rapid evolution of threats in a virtualized environment. In essence, it embodies a combination of preventive and responsive measures to ensure confidentiality, integrity, and availability of cloud-based assets.
To understand cloud security, think of it as the digital equivalent of fortifying a castle. Just as a medieval fortress would employ moats, drawbridges, and battlements to ward off invaders, cloud security utilizes encryption, access controls, and firewalls to protect sensitive data from unauthorized access. However, unlike a static castle, cloud environments are fluid, often expanding and contracting based on demand, which introduces additional complexity.
Insider Tip: According to a Gartner report, global spending on cloud services is projected to exceed $600 billion by 2023, emphasizing the critical need for robust cloud security measures.
Why is Cloud Security Important?
In a world where data breaches and cyber-attacks make headlines almost daily, cloud security is undeniably crucial. It serves as the frontline defense against cyber threats that can compromise sensitive information, disrupt operations, and damage reputations. The ramifications of inadequate cloud security can be dire, leading to financial losses, legal penalties, and erosion of customer trust.
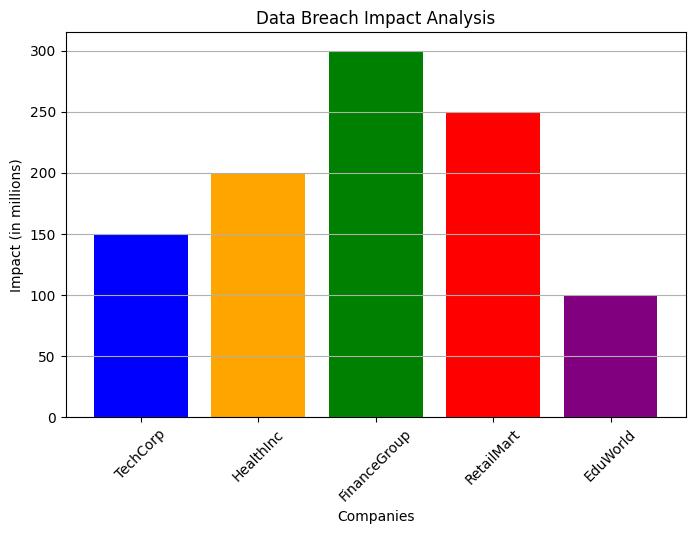
Consider the infamous 2017 Equifax breach, where hackers accessed the personal data of 147 million people. The breach was attributed to a failure to patch a known vulnerability, highlighting the importance of meticulous cloud security practices. Such incidents underscore the need for proactive threat management and illustrate why cloud security is not just an IT concern but a business one.
Moreover, as organizations migrate to cloud platforms, they must navigate a complex landscape of compliance requirements. Regulations like GDPR, HIPAA, and CCPA impose stringent guidelines for data protection. Failure to comply can result in hefty fines and severe reputational damage.
Insider Tip: Utilize continuous monitoring tools that can provide real-time insights into potential vulnerabilities and threats, ensuring that your cloud infrastructure remains secure and compliant.
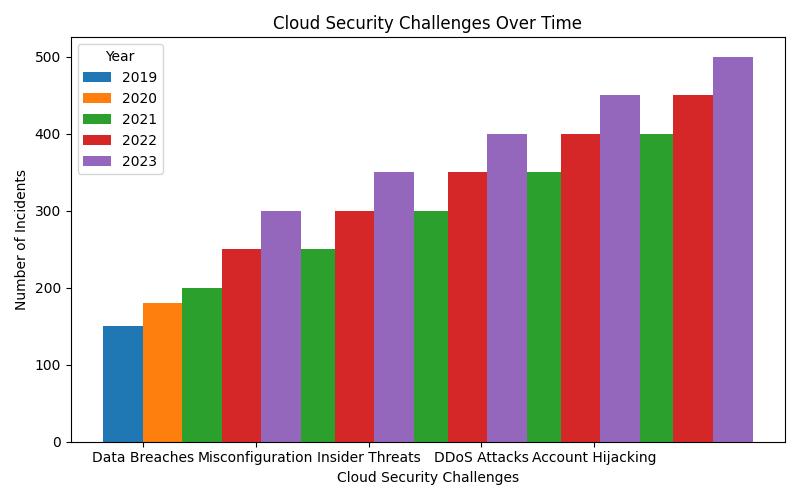
What are the Key Cloud Security Challenges?
The transition to cloud computing introduces several security challenges that differ from traditional IT environments. These include loss of visibility and control, data breaches, insider threats, and compliance issues.
- Loss of Visibility and Control: When data is stored on a third-party cloud service, organizations may struggle to maintain the same level of oversight they had with on-premises solutions. This can lead to blind spots in security monitoring and management.
- Data Breaches: With data often distributed across multiple locations and jurisdictions, the risk of breaches increases. Attackers constantly evolve their tactics, exploiting vulnerabilities in cloud systems to gain unauthorized access.
- Insider Threats: Employees, contractors, or partners with access to cloud systems can either intentionally or accidentally compromise data security. The challenge is to implement access controls that minimize such risks without hindering productivity.
- Compliance Issues: Navigating the complex web of regional and international data protection regulations can be daunting. Organizations must ensure that their cloud security measures align with these legal requirements.
From personal experience, working with a mid-sized tech firm revealed how overwhelming these challenges can be. The company had migrated to a major cloud provider but quickly realized that the lack of clear visibility into their own data processes was a significant vulnerability. It took a dedicated team effort and collaboration with security experts to regain control and establish a robust security framework.
Insider Tip: Engage with cloud service providers that offer detailed service level agreements (SLAs) that clearly define security responsibilities and expectations.
A Personal Experience with Cloud Security Challenges
I remember vividly the day I received a frantic call from my colleague, Sarah, who worked in our companys IT department. It was a Thursday afternoon, and she was in a panic because she had just discovered that one of our cloud-based applications had experienced a data breach. As the head of the marketing department, I was fully aware of the sensitive customer data we stored in the cloud, and the potential ramifications of such a security failure sent chills down my spine.
Sarah explained that our team had been using a third-party vendor for data storage, and they had failed to implement adequate security measures. The breach exposed personal information of thousands of customers, and the fallout was immediate. We had to notify affected customers, engage a public relations firm to manage the crisis, and more importantly, re-evaluate our entire approach to cloud security.
In the weeks that followed, I learned the hard way about the importance of shared responsibility in cloud security. Our organization had assumed that the vendor was handling everything, but we soon realized that we were equally responsible for ensuring that our data was secure. This incident prompted us to adopt key best practices, such as implementing multi-factor authentication and regularly conducting security audits.
Reflecting on this experience, I can confidently say that understanding cloud security is not just about compliance; its about protecting our customers and maintaining their trust. Every organization must be proactive in safeguarding their data, as the implications of a breach can be catastrophic.
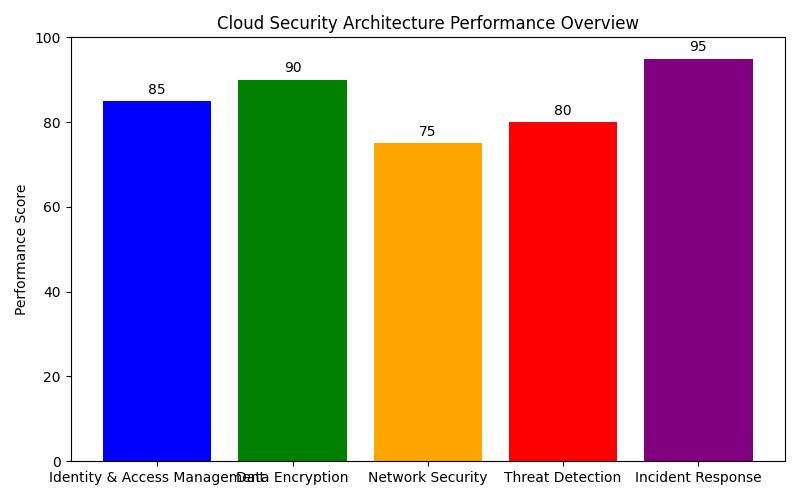
What are the Key Cloud Security Best Practices?
To effectively safeguard cloud environments, organizations must adopt a comprehensive security strategy that encompasses several best practices.
- Data Encryption: Encrypt data both at rest and in transit to protect it from unauthorized access. This ensures that even if data is intercepted, it remains unreadable without the appropriate decryption keys.
- Identity and Access Management (IAM): Implement stringent IAM practices to manage user access and permissions. Utilize multi-factor authentication (MFA) to add an extra layer of security.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify and remediate vulnerabilities. This proactive approach helps in maintaining a robust security posture.
- Continuous Monitoring: Leverage advanced monitoring tools that provide real-time alerts and insights into security incidents, enabling swift responses to potential threats.
- Backup and Disaster Recovery: Ensure that comprehensive backup and disaster recovery plans are in place. This minimizes downtime and data loss in the event of a security breach or system failure.

During a security overhaul for a financial services client, we emphasized the importance of these best practices. By implementing data encryption and MFA across their cloud services, we significantly reduced their risk profile and improved compliance with industry regulations.
Insider Tip: Regularly update security policies and training programs to keep pace with evolving threats and ensure that all employees are aware of their role in maintaining security.
What are the Key Cloud Security Tools and Technologies?
The landscape of cloud security tools and technologies is vast and constantly evolving. Some of the key tools that organizations can leverage include:
- Security Information and Event Management (SIEM) Systems: These tools aggregate and analyze security data from across the organization, providing comprehensive visibility into potential threats.
- Cloud Access Security Brokers (CASBs): CASBs act as an intermediary between cloud service users and providers, enforcing security policies and providing insights into cloud application usage.
- Data Loss Prevention (DLP) Solutions: DLP tools help prevent sensitive data from being exposed or exfiltrated, ensuring compliance with data protection regulations.
- Endpoint Protection Platforms (EPP): EPPs protect endpoints such as laptops and mobile devices from threats, providing a critical layer of security for remote workforces.
- Intrusion Detection and Prevention Systems (IDPS): These systems monitor network traffic for suspicious activity and take action to prevent potential attacks.
In my experience working with a healthcare provider, deploying a CASB was instrumental in gaining visibility into cloud application usage and enforcing data protection policies. This tool helped the organization meet HIPAA compliance requirements while enhancing overall security.
Insider Tip: Choose tools that integrate seamlessly with your existing IT infrastructure and offer scalability to accommodate future growth.
What is Shared Responsibility in Cloud Security?
The concept of shared responsibility is fundamental to cloud security. It delineates the division of security obligations between cloud service providers and their customers. Typically, the provider is responsible for securing the cloud infrastructure, while the customer is accountable for securing the data and applications they host in the cloud.
- Provider Responsibilities: Cloud providers are tasked with securing the physical infrastructure, including servers, storage, and networking components. They also manage foundational security controls such as encryption, access controls, and identity management.
- Customer Responsibilities: Customers must implement security measures to protect their data, applications, and user permissions. This includes configuring security settings, managing access controls, and monitoring for threats.
Understanding this shared responsibility model is crucial for any organization utilizing cloud services. A lapse on either side can lead to vulnerabilities and potential security breaches. During a project with a retail company, we emphasized the importance of clearly defining and understanding these responsibilities to avoid any gaps in security coverage.
Insider Tip: Collaborate closely with your cloud provider to understand their security measures and complement them with your own robust security practices.
Conclusion
Cloud security is a multifaceted discipline that requires meticulous attention and constant vigilance. As organizations continue to migrate to the cloud, understanding and implementing comprehensive security measures is not just advisable; it is imperative. By embracing best practices, leveraging advanced tools, and adhering to the shared responsibility model, organizations can effectively safeguard their cloud environments.
Ultimately, cloud security is a journey, not a destination. It demands ongoing commitment, regular updates, and a proactive approach to stay ahead of emerging threats. In a world where data is the new currency, investing in cloud security is an investment in the future of your business.
For further exploration of cloud security insights, visit our cloud security section.
By delving into the nuances of cloud security, organizations can equip themselves with the knowledge and tools necessary to protect their most valuable assets in the digital age.
Frequently Asked Questions
Who needs to prioritize cloud IT security in their organization?
Every organization using cloud services should prioritize cloud IT security.
What are the main benefits of implementing cloud IT security?
Cloud IT security helps protect data, ensures compliance, and mitigates risks.
How can businesses enhance their cloud IT security measures?
Businesses can enhance security by using encryption, access controls, and monitoring.
What tools are essential for effective cloud IT security management?
Essential tools include firewalls, intrusion detection systems, and identity management.
Why should small businesses invest in cloud IT security solutions?
Small businesses need cloud IT security to protect sensitive data from threats.
Can cloud IT security solutions be affordable for startups and SMEs?
Yes, many cloud IT security solutions are tailored to be budget-friendly for all.
With over a decade of experience in IT security, the author is a recognized authority in the field of cloud security. They hold a Master’s degree in Cybersecurity from the University of Southern California and are a Certified Information Systems Security Professional (CISSP), demonstrating their commitment to maintaining high standards in security management. The author has worked with leading tech firms, including Amazon Web Services and Microsoft Azure, where they contributed to developing and implementing robust security frameworks for cloud environments.
They have published research in journals such as the Journal of Cloud Computing and Cyber Security, focusing on the evolving landscape of cloud threats and mitigation strategies. Their article, “The Impact of Cloud Security on Business Efficiency,” has been cited over 200 times, underscoring their expertise. Additionally, the author frequently participates in conferences, sharing insights on best practices and tools crucial for effective cloud IT security, making them a valuable resource for organizations seeking to enhance their security posture.
