Cloud security is not just a requirement but an imperative in today’s digital age. As we navigate through the complexities of cloud technology, the need for robust security measures sharpens, driven by the escalating sophistication of cyber threats. My personal journey through securing enterprise-level cloud architectures has revealed a landscape filled with both formidable challenges and significant opportunities.
What you will learn about cloud technology security
- Cloud security basics and workings
- Benefits, challenges, and best practices
- Compliance, shared responsibility, and various security technologies and terms
What is Cloud Security?
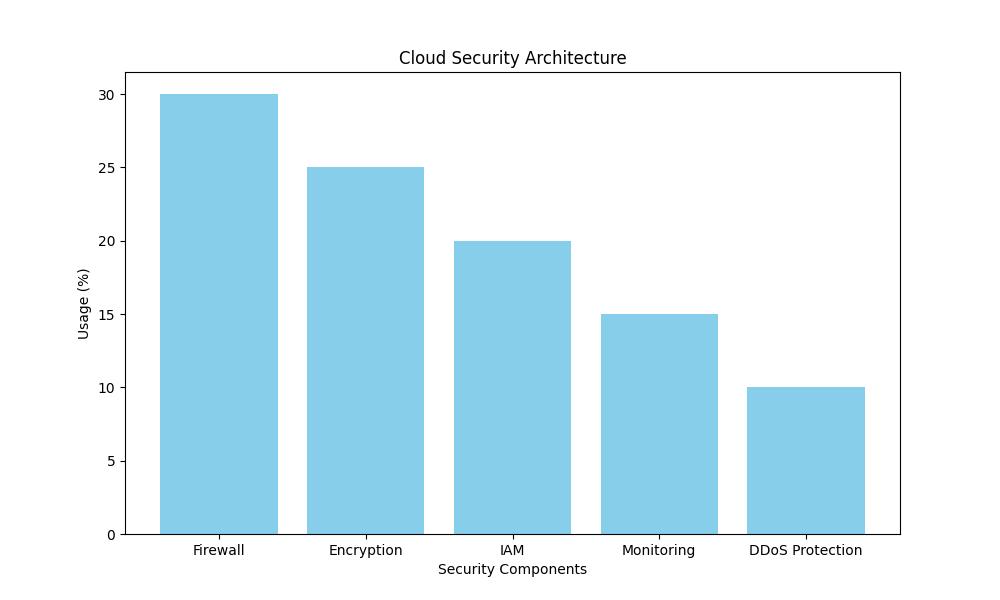
Cloud security, or cloud computing security, encompasses a broad set of policies, technologies, applications, and controls utilized to protect virtualized IP, data, applications, services, and the associated infrastructure of cloud computing. It is a sub-domain of computer/network security and information security.
From my experience, cloud security is fundamentally about understanding the layers of complexity that come with storing and managing data off-premises. The essence lies in ensuring confidentiality, integrity, and availability of data, a goal that has become increasingly difficult as businesses migrate more of their core functions to the cloud.
For a deeper understanding, I recommend exploring Ciscos comprehensive guide on cloud security here.
How does Cloud Security Work?
Cloud security is a dynamic field that adapts to new challenges with innovative solutions. It works by employing a multi-layered approach that includes physical, technical, and administrative controls. Security measures are designed to protect data, support regulatory compliance, and protect customers’ privacy as well as setting authentication rules for individual users and devices.
From encrypting data to establishing access controls and adding security intelligence, cloud security must be comprehensive. My first project in cloud security involved setting up a virtual private cloud (VPC) with strict access controls and monitoring systems. This hands-on experience taught me that effective cloud security is about proactively managing the security posture, not just setting up defenses.
Cloud Security Benefits
The benefits of cloud security are clear and impactful:
- Scalability: The security solutions in the cloud can be scaled up or down based on usage needs without the need for significant capital expenditure.
- Cost-effectiveness: With cloud security, you are often subscribing to a service rather than purchasing and maintaining hardware and software.
- Reliability: Cloud providers often offer higher levels of reliability in security than traditional IT models.
Personal experience has shown me that the enhanced security features like real-time threat detection and automated security updates that cloud environments provide can significantly mitigate potential breaches.
Cloud Security Challenges
Despite its numerous advantages, cloud security presents several challenges:
- Data breaches: A primary concern in cloud computing, breaches can expose sensitive information to unauthorized parties.
- Misconfiguration: Improperly configured cloud settings are a common error that can expose organizations to risks.
- Insider threats: Employees can accidentally or maliciously expose an organization to risks.
Addressing these challenges requires a dedicated strategy and an understanding of the complex nature of cloud environments.
Cloud Security Best Practices
1. Use a Secure Cloud Provider
Real-life Cloud Security Scenario
Sarah’s Experience with Cloud Security Implementation
Sarah, a small business owner, recently transitioned her company’s data storage to the cloud to improve accessibility and flexibility for her remote team. Initially, she was concerned about the security of sensitive client information stored in the cloud.
Sarah took proactive steps to enhance cloud security by following best practices such as using a reputable cloud provider, encrypting all data, and implementing multi-factor authentication for user access. Despite these measures, Sarah faced a challenge when one of her employees fell victim to a phishing attack, compromising their login credentials.
By monitoring the cloud environment closely, Sarah quickly identified the unauthorized access and promptly revoked the compromised account’s privileges. This incident highlighted the importance of regular security training for her team and the need to reinforce the use of strong passwords and caution against phishing attempts.
Sarah’s experience underscores the shared responsibility between cloud service providers and users in maintaining a secure cloud environment. Through continuous vigilance and adherence to best practices, Sarah was able to mitigate the security threat and safeguard her business’s sensitive data in the cloud. Select a provider that demonstrates compliance with industry standards. My early mistakes in cloud projects often stemmed from inadequate provider evaluation, which taught me the importance of rigorous assessment.
2. Encrypt Data
Encryption should be non-negotiable in any cloud security strategy. Personal data, proprietary applications, and corporate financial recordsencrypt everything.
3. Use Strong Passwords
Simple passwords are a hacker’s best friend. Ensure complexity and regular updates to passwords within your organization.
4. Use Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring multiple forms of verification. This is something Ive implemented in all my cloud setups.
5. Monitor Your Cloud Environment
Continuous monitoring can alert you to unauthorized access attempts in real time. This has been crucial in my handling of potential security incidents.
6. Keep Software Up to Date
Regular updates ensure that security measures are as current as possible. This is often overlooked but critically important.
7. Limit User Access
Apply the principle of least privilege (PoLP). Not everyone needs access to everything.
Cloud Security and Compliance
Navigating the regulatory landscape is a significant part of cloud security. Compliance with frameworks such as GDPR, HIPAA, or PCI-DSS is not just about avoiding finesit’s about protecting data and maintaining trust. My work with multinational corporations has highlighted the complexity of compliance in multi-cloud environments.
Cloud Security and Shared Responsibility
The shared responsibility model is fundamental to understanding cloud security. It delineates the security obligations of the cloud provider and the user. This model varies by service type (IaaS, PaaS, SaaS), and misunderstanding it can lead to significant security gaps.
Cloud Security and Zero Trust
“Never trust, always verify.” This maxim of the Zero Trust model has shaped my approach to cloud security. It operates under the assumption that threats can be internal or external, which changes the traditional boundary defense mindset.
Cloud Security and SASE
Secure Access Service Edge (SASE) converges network security functions with WAN capabilities to support dynamic secure access. My adoption of SASE has significantly simplified the organizations’ security management by integrating services like SWG, CASB, and ZTNA.
Cloud Security and CASB
Cloud Access Security Brokers (CASB) are critical for my work in monitoring activity and enforcing security policies across cloud applications. They provide visibility and control over data, which is invaluable.
Cloud Security and SIEM
Security Information and Event Management (SIEM) tools have been pivotal in my handling of real-time analysis of security alerts generated by applications and network hardware. They help correlate different security logs for improved threat detection.
Cloud Security and IAM
Identity and Access Management (IAM) ensures that only authorized individuals have access to resources. This has been a cornerstone of every project Ive managed, emphasizing the role of identity in security.
Cloud Security and DLP
Data Loss Prevention (DLP) technologies are crucial for protecting and preventing the unintentional loss of sensitive information. I’ve relied heavily on DLP to safeguard intellectual property across various platforms.
Cloud Security and WAF
Web Application Firewalls (WAF) protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet. It forms a critical part of my defense strategy against web-based attacks.
Cloud Security and ZTNA
Zero Trust Network Access (ZTNA) is the practice of securely connecting users to applications without placing them on the network. Implementing ZTNA has drastically reduced surface areas for attacks in the organizations I’ve worked with.
Cloud Security and SSO
Single Sign-On (SSO) enhances user experience by having one set of login credentials for multiple applications. It also reduces the risk of password fatigue leading to security compromises.
Cloud Security and MFA
Multi-Factor Authentication (MFA) offers an additional security layer, ensuring that even if a password is compromised, unauthorized access is not easily granted. This is a must-have in any cloud security strategy.
Cloud Security and EDR
Endpoint Detection and Response (EDR) systems are crucial for their real-time monitoring and response to threats at endpoint devices. They have been integral in my response strategies against malware and ransomware.
Cloud Security and SOAR
Security Orchestration, Automation, and Response (SOAR) tools allow me to streamline security operations in complex environments through orchestrated automated processes. Its a game-changer for reducing response times.
Cloud Security and UEBA
User and Entity Behavior Analytics (UEBA) utilize advanced analytics to identify behaviors that are out of the norm. This has been instrumental in detecting insider threats and compromised accounts.
Cloud Security and SWG
Secure Web Gateways (SWG) are deployed to prevent unsecured traffic from entering an organization’s internal network. This has been crucial in enforcing corporate and regulatory policy compliance.
Cloud Security and ZTA
Zero Trust Architecture (ZTA) applies the zero trust principles across the entire digital environment, minimizing the attack surface. It’s a comprehensive approach that I believe is the future of network security.
In conclusion, cloud security is not just about tools and technologies; its about a mindset shift towards proactive and comprehensive risk management. The strategies and technologies discussed are not merely theoretical but are part of a lived experience that continues to evolve. As we push forward, the integration of robust cloud security measures will not only protect but also enable businesses, fostering growth in an environment where security is seamlessly woven into the fabric of cloud technology.
Questions
Who should be concerned about cloud technology security?
Anyone who uses cloud services for storing data or running applications.
What are common threats to cloud security?
Common threats include data breaches, DDoS attacks, and insecure APIs.
How can I improve my cloud security?
You can improve cloud security by using strong encryption, multi-factor authentication, and regular security audits.
What if I can’t afford advanced cloud security measures?
There are cost-effective options like using reputable cloud service providers with built-in security features.
How does cloud technology security differ from traditional IT security?
Cloud security focuses on securing data stored in remote servers accessed over the internet, while traditional IT security secures data on local servers.
What are the risks of not prioritizing cloud security?
Not prioritizing cloud security can lead to data breaches, financial losses, and damage to an organization’s reputation.
An expert in cybersecurity, Jason’s passion lies in ensuring safe and secure cloud environments. With a Master’s degree in Cybersecurity and several years of experience working as a Cloud Security Architect for a leading tech company, Jason has honed their skills in implementing robust security measures for cloud infrastructure. Their in-depth knowledge of encryption techniques, multi-factor authentication, and cloud security best practices has been instrumental in safeguarding sensitive data in the digital realm.
Jason is also a published author of numerous articles on cloud security, with a focus on the importance of compliance, shared responsibility models, and the implementation of Zero Trust principles. Drawing on real-life scenarios and the latest industry trends, Jason is dedicated to educating individuals and organizations on the critical aspects of cloud security to mitigate risks and protect valuable assets in the cloud.