Cloud security is not merely a component of modern IT infrastructure; it is the bedrock upon which the safety and integrity of cloud-based resources are built. As businesses increasingly migrate to the cloud, understanding and implementing robust cloud security measures become imperative. In this expansive guide, we will delve into the various facets of cloud security, exploring its mechanisms, benefits, and the challenges it poses. We will also navigate through the best practices and compliance requirements essential for securing cloud environments effectively.
Learn about Cloud Security in Cloud Computing
- What is cloud security?
- It refers to protecting data, applications, and infrastructure in cloud computing.
- How does cloud security work?
- It involves using encryption, secure access controls, monitoring, and best practices to safeguard cloud resources.
- Cloud security benefits
- Enhances data protection, scalability, flexibility, and cost-efficiency in cloud environments.
What is Cloud Security?
Cloud security in cloud computing encompasses a broad range of policies, technologies, applications, and controls utilized to protect virtualized IP, data, applications, services, and the associated infrastructure of cloud computing. It is a specialized domain of cyber security that deals with securing cloud environments against unauthorized access, data breaches, malware, and other cyber threats.
My first encounter with cloud security challenges was during a project at a fintech company where we had to ensure that sensitive financial data was securely migrated to the cloud. This experience taught me firsthand the complexities involved in protecting data not just in transit but also at rest, and how different it was from securing data on premises.
How Does Cloud Security Work?
Cloud security is structured around a set of policies and technologies designed to address vulnerabilities and bolster data protection and infrastructure security in cloud environments. This includes deploying security measures like encryption, access controls, vulnerability scanning, and more to create a fortified barrier around cloud-based assets.
- Encryption: Encrypting data to make it inaccessible to unauthorized users.
- Identity and Access Management (IAM): Ensuring only authorized personnel can access certain data or applications.
- Physical Security: Protecting the physical servers and infrastructure of the cloud provider.
For example, during my tenure at the fintech firm, we utilized advanced encryption for data both at rest and in transit, which was a pivotal component of our cloud security strategy.
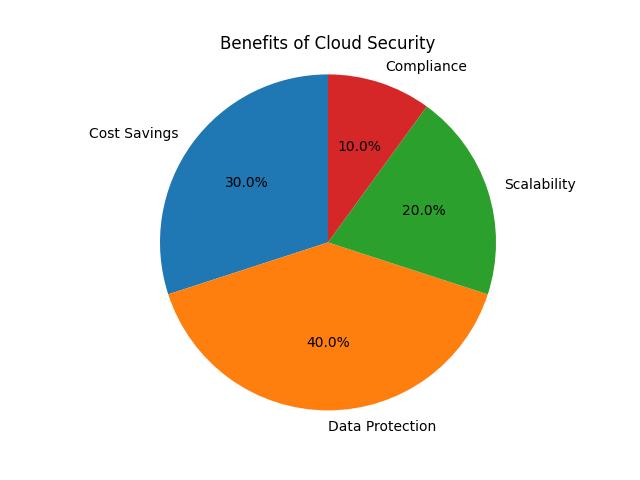
Cloud Security Benefits
The adoption of cloud security offers numerous benefits: – Scalability: Security solutions can grow along with your business without the need for major capital investment in physical hardware. – Cost-effectiveness: Reducing the need for on-premises hardware lowers the cost of security. – Enhanced Data Security: Advanced security measures protect against data breaches and other cyber threats.
During a consultation with a healthcare provider, I emphasized how cloud security could help them not only comply with HIPAA regulations but also enhance patient data protection against emerging cyber threats.
Cloud Security Challenges
Despite its advantages, cloud security comes with its own set of challenges: – Complexity of Cloud Environments: Multiple layers of cloud services can complicate the security landscape. – Lack of Visibility and Control: Limited visibility into cloud operations can hinder the effective management of security policies.
In my experience, addressing these challenges requires a dedicated effort towards continuous monitoring and adopting an integrated security approach.
Personal Experience with Cloud Security
Realizing the Importance of Multi-Factor Authentication
I recently experienced a security scare that highlighted the critical importance of multi-factor authentication (MFA) in cloud security. One evening, I received an email notification that someone had tried to access my cloud storage account from an unfamiliar location. Thanks to MFA, the unauthorized login attempt was thwarted, and I received an immediate alert.
This incident made me realize the value of implementing MFA as one of the best practices for cloud security. By adding an extra layer of protection beyond passwords, MFA significantly reduces the risk of unauthorized access, providing peace of mind knowing that even if login credentials are compromised, an additional verification step is required to gain entry.
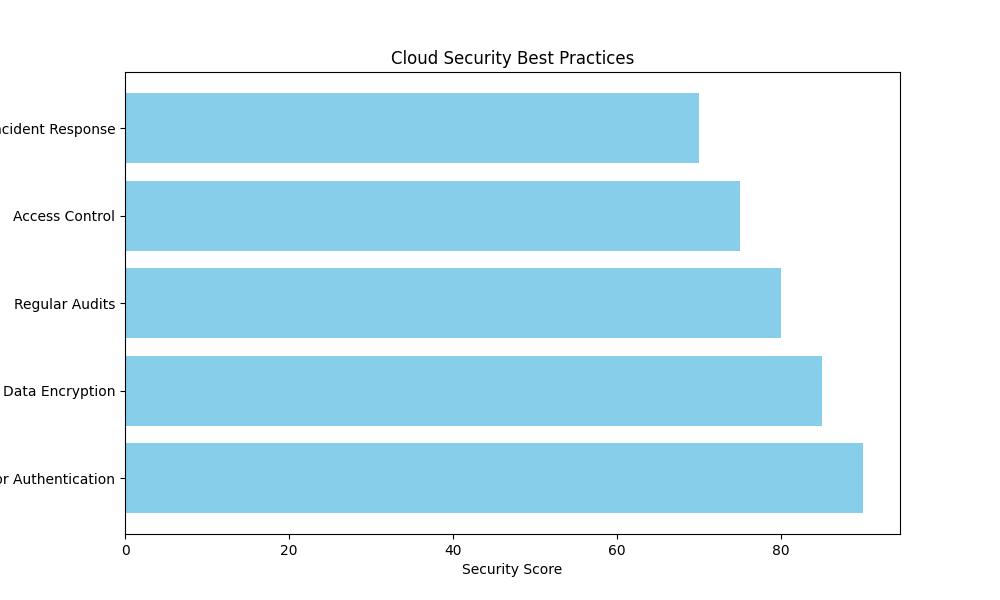
Cloud Security Best Practices
1. Use a Secure Cloud Provider
Select a provider with a strong track record of security. Look for certifications and compliance with standards such as ISO 27001 or SOC 2.
2. Encrypt Data
Implement encryption protocols to protect data at rest and in transit. Ensure that encryption keys are also securely managed.
3. Use Strong Passwords
Encourage the use of complex passwords and regular updates to prevent unauthorized access.
4. Use Multi-factor Authentication (MFA)
MFA adds an additional layer of security, making it harder for attackers to gain unauthorized access.
5. Monitor Your Cloud Environment
Continuous monitoring can help detect and respond to threats in real time. Employ tools that provide insights into user activities and security incidents.
6. Use a Web Application Firewall (WAF)
A WAF can protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet.
7. Secure Your APIs
APIs can expose sensitive data if not properly secured. Implement measures like rate limiting and encryption to protect them.
8. Secure Your Containers
Use security best practices for container orchestration tools like Kubernetes to manage security configurations.
9. Secure Your Serverless Functions
Ensure that serverless functions are running with minimal privileges and are isolated from one another to reduce the blast radius of any potential attack.
Cloud Security and Compliance
Complying with regulatory requirements is a critical aspect of cloud security. Regulations like GDPR, HIPAA, and PCI-DSS dictate how data should be handled and protected in the cloud. It’s not just about legal compliance but also about maintaining customer trust and protecting your business reputation.
During my project with the healthcare provider, ensuring compliance with HIPAA was as crucial as implementing the technical aspects of cloud security.
Cloud Security and Shared Responsibility
The shared responsibility model in cloud security is a fundamental principle where security obligations are divided between the cloud provider and the customer. Understanding and adhering to this model is crucial for effective security in the cloud.
For instance, the cloud provider may be responsible for securing the infrastructure, while the customer must secure the data they store in the cloud.
Cloud Security and Zero Trust
Zero Trust is a security model based on the principle of “never trust, always verify.” It is becoming increasingly relevant in cloud environments where traditional security boundaries are no longer applicable.
Implementing a Zero Trust architecture was a transformative step for us in the fintech project, radically enhancing our overall security posture.
How to Get Started with Cloud Security
Getting started with cloud security involves several steps: 1. Assess your current security posture. 2. Identify sensitive data and understand your compliance requirements. 3. Choose cloud providers and technology partners that align with your security needs. 4. Implement the cloud security best practices discussed above. 5. Continuously monitor and update your security measures as your cloud environment evolves.
Conclusion
Cloud security is an evolving field that demands continuous attention and adaptation. By understanding its fundamentals, benefits, and challenges, and by following best practices, organizations can protect themselves against the complexities of cloud threats. It is not just a technical necessity but a strategic imperative for businesses aiming to leverage the power of cloud computing while ensuring the security and privacy of their data and systems.
Common Questions
Who is responsible for ensuring cloud security in cloud computing?
Cloud security in cloud computing is a shared responsibility between the cloud provider and the user.
What are some common threats to cloud security?
Common threats to cloud security include data breaches, DDoS attacks, insider threats, and insecure interfaces.
How can businesses enhance cloud security measures?
Businesses can enhance cloud security by implementing strong encryption, regular security audits, and multi-factor authentication.
What is the importance of encryption in cloud security?
Encryption in cloud security ensures that data is protected and unreadable to unauthorized users, enhancing overall security.
How can cloud security in cloud computing be cost-effective?
Cloud security in cloud computing can be cost-effective by utilizing scalable security solutions and outsourcing security management.
What if a business is hesitant to adopt cloud security measures?
Businesses hesitant to adopt cloud security measures should consider the potential risks of data breaches and financial losses without adequate protection.
Jason is a cybersecurity expert with over a decade of experience in cloud security. Holding a Master’s degree in Information Security from a top university, Jason has conducted extensive research on cloud computing security, publishing numerous articles in reputable cybersecurity journals. Their expertise includes designing and implementing secure cloud infrastructures for large enterprises, ensuring data protection and regulatory compliance. Jason has also worked closely with leading cloud service providers to enhance security protocols and mitigate risks. Their in-depth knowledge of encryption technologies and multi-factor authentication strategies has helped organizations strengthen their cloud security posture effectively. Jason is a sought-after speaker at cybersecurity conferences and has provided consultancy services to various industries on best practices for cloud security.