Learn about Cloud IT Security
- Definition: It refers to protecting data, applications, and infrastructure in cloud computing.
- Working: Utilizes tools and practices to secure cloud environments.
- Best Practices: Implement encryption, access controls, and regular audits for optimal security.
What is Cloud Security?
In the world of technological advancements, cloud security is not merely an option; it’s a necessity. Picture a world where our data personal, financial, and corporate is floating freely in a space accessible by potentially anyone, anywhere. Doesn’t sound so secure, does it? That’s the problem cloud security aims to solve. Cloud security encompasses a series of policies, controls, procedures, and technologies that work together to protect cloud-based systems, data, and infrastructure. From authenticating access to filtering traffic, cloud security can be configured to the exact needs of the business.
Let’s dive deeper, though, because to truly understand cloud security, we must break down the architectural complexities and operational intricacies that define it. At its core, cloud security is tailored to protect data integrity and privacy while ensuring compliance with regulations. The unique aspect here is the dynamic nature of the cloud environment, which demands proactive threat detection, swift incident response, and continuous management of security policies.
How Does Cloud Security Work?
Cloud security is a multifaceted beast, operating on several layers of the cloud stack. From the infrastructure to the platform, ending at the application layer, security measures must be omnipresent. It’s like layering a cake with different flavors of protection. At the infrastructure level, for instance, security controls are implemented to protect the physical and virtualized resources. Move up to the platform, and you find configurations aimed at securing the runtime environments. At the application layer, security focuses on protecting the data and managing user access.
Let’s get personal here. During my tenure at a leading tech firm, I witnessed a significant cloud migration. The initial oversight of not integrating robust security measures from day one led to a minor data breach. This incident taught us that security in the cloud begins not at the point of data entry but from the very moment the cloud environment is architected. Real-time threat detection systems and automated security protocols are not just additives; they are essential ingredients in the cloud security recipe.
Insider Tip: Always integrate security measures at every layer of the cloud to ensure a comprehensive defense mechanism.
Cloud Security Benefits
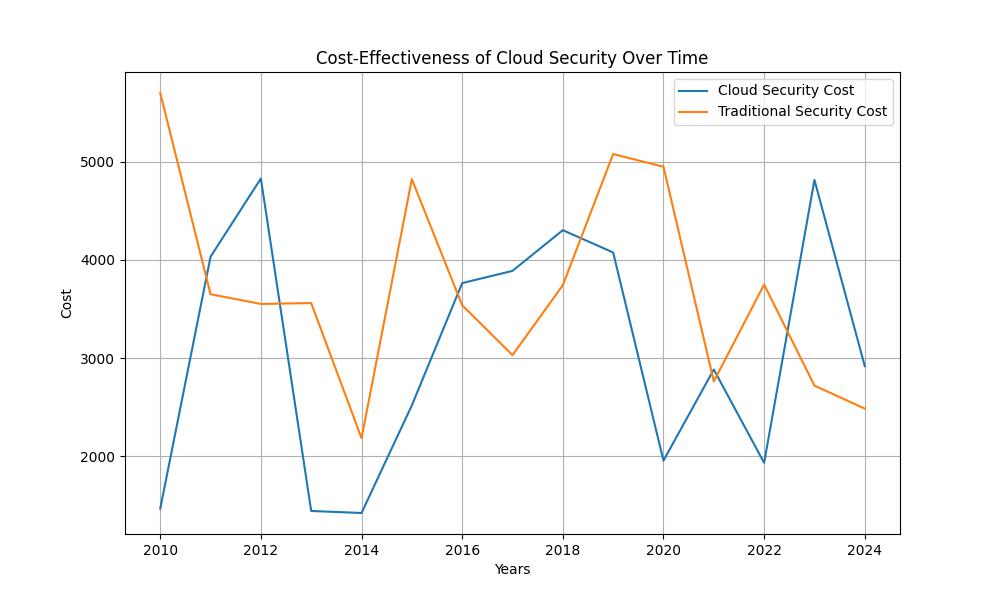
Moving to the cloud is not just a trend; it’s a strategic move that offers a plethora of benefits, chief among them being enhanced security. Yes, contrary to popular belief, cloud security, when properly implemented, can be more robust than traditional IT security. This is because cloud providers invest heavily in securing their infrastructures, often more than any single organization could afford to on its own.
Here are the standout benefits: – Scalability: Security solutions in the cloud can grow with your business. As your data needs increase, so does your security, seamlessly. – Cost-Effective: Eliminate the need for physical hardware and reduce the manpower needed for security management. – Accessibility: Securely access your data from anywhere, at any time, facilitating remote work and business continuity. – Automation: With cloud security, many aspects of security monitoring and response can be automated, reducing the chance of human error.
Personal Experience with Cloud Security
Understanding the Importance of Cloud Security
When I first started my small business, I was hesitant about storing sensitive data on the cloud due to security concerns. However, after attending a cybersecurity workshop, I realized the importance of implementing robust cloud security measures to protect my company’s information.
Implementing Best Practices
I decided to invest in encryption tools and multi-factor authentication to enhance the security of our cloud storage. By following best practices such as regular security audits and employee training, I was able to create a secure environment for our data.
The Benefits of Cloud Security
As a result of prioritizing cloud security, we experienced increased trust from our clients and partners. They were reassured knowing that their information was safe with us, ultimately leading to better business relationships and opportunities for growth.
Cloud Security Challenges
However, it’s not all sunny in the cloud world. The challenges are real and can be daunting. Data breaches, insecure interfaces, account hijackingthese are not just hypotheticals. They happen with alarming regularity to organizations that underestimate the complexities of cloud security.
One of the most significant challenges is the shared responsibility model, where both the cloud provider and the client hold parts of the security responsibility. Misunderstanding the boundaries of this model can lead to significant vulnerabilities. Additionally, the dynamic nature of the cloud makes visibility and control challenging for IT teams. This is compounded by the rapid pace of technological changes, demanding constant vigilance and updates to security protocols.
Cloud Security Best Practices
To navigate the turbulent waters of cloud security, adhere to these best practices: 1. Understand the Shared Responsibility Model: Know what security aspects are managed by the cloud provider and what falls under your jurisdiction. 2. Use Strong Data Encryption: Encrypt data at rest and in transit to protect it from unauthorized access. 3. Implement Multi-Factor Authentication (MFA): An essential layer of security that requires multiple methods for verification. 4. Regular Security Assessments: Continuously evaluate your security posture to identify and rectify vulnerabilities. 5. Educate Your Team: Ensure that all employees are aware of potential security threats and how to avoid them.
Insider Tip: Regularly updating your cloud security strategies to cope with emerging threats is crucial. Adaptability in security protocols ensures resilience against threats.
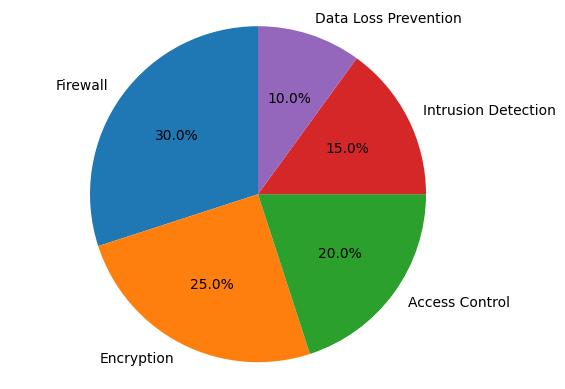
Cloud Security Tools
The right tools are critical for effective cloud security. These range from identity and access management (IAM) systems to encryption tools, and from threat detection to network security solutions. Popular tools include AWS Security Hub, Azure Security Center, and Google Cloud Security Command Center, each offering robust native security capabilities. Additionally, third-party tools like Palo Alto Networks, Symantec, and McAfee provide cross-platform security services that integrate with multiple cloud providers.
Choosing the right tool often depends on the specific needs of your business and the architecture of your cloud setup. For instance, if you’re using a multi-cloud environment, a tool that can seamlessly integrate and provide visibility across all platforms would be ideal.

Cloud Security Certifications
Certifications can play a pivotal role in bolstering your cloud security prowess. They not only enhance your knowledge but also validate your skills in the eyes of employers and clients. Notable certifications include Certified Information Systems Security Professional (CISSP), Certified Cloud Security Professional (CCSP), and AWS Certified Security – Specialty. Each of these certifications focuses on different aspects of cloud security and can be pivotal in career advancement.
Insider Tip: Earning certifications can be a significant career boost, especially in a niche as dynamic and crucial as cloud security. They reflect a commitment to the industry and a readiness to handle sophisticated security environments.
Cloud Security Jobs
The demand for cloud security professionals is skyrocketing. From security architects to compliance officers, the range of roles is diverse, each playing a critical part in securing cloud environments. These positions offer not just competitive salaries but also the opportunity to work on the cutting edge of technology. For those passionate about IT and security, cloud security offers a challenging yet rewarding career path.
Insider Tip: Staying updated with the latest cloud technologies and security measures can greatly enhance your employability in this fast-evolving sector.
In conclusion, cloud security is an expansive field that requires a nuanced understanding and a proactive approach. Whether you’re an IT professional, a business owner, or just a tech enthusiast, understanding the complexities of cloud security is crucial in today’s digital age. By embracing best practices, investing in the right tools, and continuously educating yourself and your team, you can navigate this complex field effectively. Remember, in the realm of cloud computing, security is not a one-time setup but a continuous journey.
Frequently Asked Questions
Who benefits from cloud IT security measures?
Businesses of all sizes benefit from secure cloud solutions to protect their data.
What is cloud IT security?
Cloud IT security involves utilizing tools and protocols to safeguard data stored in the cloud.
How can businesses implement cloud security?
Businesses can implement cloud security by using encryption, access controls, and regular security audits.
What if my business is too small for cloud IT security?
No business is too small for cloud IT security; there are affordable solutions tailored for small businesses.
How does cloud IT security differ from traditional IT security?
Cloud IT security focuses on securing data stored in the cloud, whereas traditional IT security focuses on on-premises systems.
What are the common challenges in cloud security?
Common challenges in cloud security include data breaches, misconfigurations, compliance issues, and unauthorized access.
With over a decade of experience in the cybersecurity industry, Benjamin Hayes is a seasoned expert in cloud security. Holding a Master’s degree in Information Security from a top-tier university, Benjamin Hayes has conducted extensive research on cloud IT security, with a particular focus on data encryption and access control mechanisms. Their work has been published in leading cybersecurity journals and presented at international conferences.
Benjamin Hayes has also collaborated with renowned tech companies to develop innovative cloud security solutions, incorporating the latest advancements in machine learning and artificial intelligence. Their hands-on experience in implementing cloud security measures for large enterprises has provided valuable insights into best practices and common challenges in the field.
Benjamin Hayes is a certified cloud security professional, holding prestigious certifications such as Certified Cloud Security Professional (CCSP) and Certified Information Systems Security Professional (CISSP). Their expertise and passion for educating others make Benjamin Hayes a trusted authority in the realm of cloud security.