Cloud security is not just an option; it’s an imperative necessity in the digital age. Any organization leveraging cloud technology needs to prioritize its security measures now more than ever. I say this not just as a precaution but from the bitter experience of data breaches that could have been avoided with robust cloud security practices.
Learn about cloud computing & security
- Cloud security involves protecting data, applications, and infrastructure in cloud computing environments.
- Benefits include scalability, cost-efficiency, and flexibility.
- Risks include data breaches, data loss, and compliance violations.
What is cloud security?
Cloud security refers to the collective measures, technologies, and policies configured to protect cloud-based systems, data, and infrastructure. From protecting data integrity through encryption to safeguarding user access with advanced authentication mechanisms, cloud security covers a holistic, multi-layered approach. I remember a time when a simple password would suffice; those days are long gone. Now, every data interaction within the cloud needs a rigorous security checkpoint.
Here’s an interesting fact: According to a report by Canalys, cloud security breaches have increased by 36% over the past year alone. This statistic alone should trigger an alarm for any organization relying on cloud solutions.
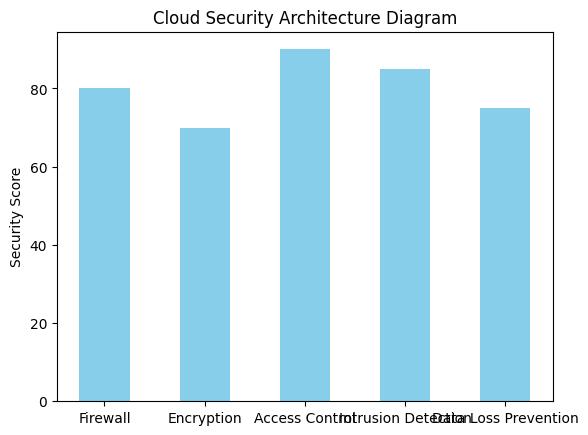
How does cloud security work?
Cloud security is a complex integration of policies, controls, procedures, and technologies that work together to protect cloud-based systems. It’s fascinating to see how these elements interact. For instance, consider the role of firewalls and intrusion detection systems that monitor and control incoming and outgoing network traffic based on predetermined security rules. This isn’t just about blocking unauthorized access; it’s about creating a resilient environment that can adapt and respond to potential threats dynamically.
A memorable project I worked on involved setting up a cloud infrastructure for a financial services firm. The integration of behavioral analytics to monitor for unusual access patterns was particularly interesting, as it combined AI with traditional security measures to enhance protection.
For a deeper dive into how these technologies mesh, this comprehensive guide provides a great starting point.
What are the benefits of cloud security?
The benefits of cloud security are manifold:
– Risk Reduction: It significantly lowers the risk of cyber threats and data breaches.
– Compliance Assurance: Helps businesses meet regulatory requirements effortlessly.
– Scalability: Security measures can be scaled according to the needs of the business, a boon for growing companies.
From my experience, one of the most significant benefits I’ve observed is the peace of mind it brings to business leaders. Knowing that sensitive data and systems are well-protected allows them to focus on business growth and operational efficiency.
What are the risks of cloud security?
No technology is without its risks, and cloud security is no exception. The primary risks include:
– Data breaches: The most common and feared risk, leading to loss of reputation and hefty fines.
– Misconfiguration: Often overlooked, simple misconfigurations can leave the door wide open for attackers.
– Insider threats: Sometimes the danger comes from within, from employees who have access to sensitive information.
I once dealt with a cloud storage misconfiguration that led to unauthorized data exposure. It was a wake-up call to tighten and regularly audit security configurations.
What are the types of cloud security?
1. Network security
This involves protecting the communications channel and ensuring that the network is impervious to unauthorized access and data breaches. Think of it as fortifying the walls of your digital castle.
2. Data security
Data is the gold of the digital era. Encrypting data at rest and in transit, ensuring only those with authorized access can view or use the data, is crucial.
3. Identity and access management (IAM)
IAM ensures that only authenticated and authorized individuals can access resources appropriately. This was a game changer in a project where we had to manage access for thousands of employees globally.
4. Application security
This secures the software that interacts with the cloud data. Regular updates and vulnerability scans are part of this package.
5. Security operations
This involves continuous monitoring and real-time analysis of security alerts generated by applications and network hardware.
How to secure your cloud environment
1. Use a secure password manager
NordPass, for example, can manage and store complex passwords securely.
2. Use multi-factor authentication (MFA)
MFA adds an extra layer of protection, making it harder for attackers to gain unauthorized access.
3. Encrypt your data
Using tools like NordLocker ensures that your data is unreadable to those who might intercept it.
4. Use a VPN
NordVPN creates a secure connection over the internet, shielding your data from cyber threats.
5. Keep your software up to date
Regular updates fix security vulnerabilities and enhance functionality.
6. Use a cloud access security broker (CASB)
CASBs provide a security policy enforcement point placed between cloud service consumers and cloud service providers to combine and interject enterprise security policies as resources are accessed.
Real-Life Cloud Security Implementation
Maria’s Experience with Cloud Security
Maria, a small business owner, decided to migrate her company’s data to the cloud for easier access and collaboration among her team. Concerned about security, she implemented various cloud security measures. Maria started by using a secure password manager to ensure strong and unique passwords for all accounts. She also enforced multi-factor authentication (MFA) for an added layer of security.
To secure sensitive client information, Maria encrypted all data before uploading it to the cloud. She also set up a VPN for secure remote access to the company’s network. Regularly updating software and employing a cloud access security broker (CASB) were essential parts of her cloud security strategy.
By following these best practices and using reliable cloud security tools like NordPass and NordVPN, Maria successfully safeguarded her business data in the cloud, giving her peace of mind and ensuring her clients’ confidentiality.
Cloud security best practices
Adopting best practices is crucial for enhancing cloud security. These include conducting regular security audits, implementing end-to-end encryption, and training employees on security protocols. Remember, the human element is often the weakest link in the security chain.
Cloud security tools and software
NordPass
Manages passwords securely and efficiently.
NordVPN
Secures internet connections and protects sensitive data in transit.
NordLocker
Encrypts files stored in the cloud, providing robust data security.
NordLayer
Offers advanced cloud security solutions tailored for businesses.
NordPass Business
Designed for enterprise-level password management.
NordVPN Teams
Provides teams with secure and private internet access.
NordLayer Business
Enhances business security with customized cloud solutions.
In conclusion, cloud security is a dynamic field that requires ongoing attention and adaptation. Implementing robust security measures can significantly mitigate risks and enhance business operations. Remember, investing in cloud security is not just about protecting data; it’s about securing your business’s future.
FAQs
Q: Who can benefit from cloud security measures?
A: Businesses of all sizes can benefit from cloud security to protect their data and systems from cyber threats.
Q: What are the common risks in cloud computing?
A: Common risks in cloud computing include data breaches, unauthorized access, data loss, and insecure APIs.
Q: How can businesses enhance cloud security?
A: Businesses can enhance cloud security by using encryption, implementing strong access controls, and regularly updating security measures.
Q: Isn’t cloud security expensive for small businesses?
A: While initial setup costs may vary, many cloud security solutions offer scalable pricing options to suit small business budgets.
Q: How does cloud security ensure data privacy?
A: Cloud security ensures data privacy through encryption, secure access controls, regular security audits, and compliance with data protection regulations.
Q: What should I consider when choosing a cloud security provider?
A: When choosing a cloud security provider, consider factors like experience, reputation, compliance certifications, and the range of security services they offer.
With a Ph.D. in Cybersecurity and over a decade of experience in cloud computing, Amelia Davis is a recognized expert in the field of information security. Their research has been published in top-tier journals, focusing on the intersection of cloud technology and data protection. Amelia Davis has conducted extensive studies on cloud security implementation and best practices, providing valuable insights for businesses and individuals looking to safeguard their digital assets. As a sought-after consultant, they have worked with numerous organizations to develop robust cloud security strategies tailored to their specific needs. Drawing from their academic background and hands-on experience, Amelia Davis offers practical advice on securing cloud environments effectively.