In the digital era, the word ‘security’ is no longer just about locks and alarms; it’s about layers, protocols, and, dare I say, clouds. Cloud IT security is not just a necessity; it’s the unsung hero of our modern online lives, safeguarding our data as it flits across the globe. So, let’s skip the pleasantries and dive straight into the heart of cloud IT security, where complexity meets necessity, and innovation is the only constant.
What you’ll learn about cloud IT security
By reading this article, you will learn:
– The definition and importance of cloud security.
– How cloud security works and its benefits.
– The challenges, best practices, tools, certifications, and job opportunities in cloud security.
What is cloud security?
Cloud security, or rather the art of it, is a sophisticated ballet of technologies, policies, controls, and services working in concert to protect cloud-based systems, data, and infrastructure. From authentication to encryption, cloud security is an umbrella term that enshrines a multitude of strategies designed to keep digital assets safe in an environment that’s as fluid as it is ubiquitous.
I remember the first time I bumped into the term ‘cloud security.’ It felt like a misnomer, an oxymoron even. How can something as ephemeral as a cloud be secure? It was a sunny afternoon when an IT pal of mine explained over coffee how cloud security is akin to a fortress in the skyonly more complex. Now, the image of that fortress, replete with firewalls and encryption spells, is etched in my mind every time I store a file online or send an email into the ether.

Insider Tip: Cloud security is not a static construct; it evolves with every technological advancement and every new threat. Think of it as a living organism that adapts to survive.
How does cloud security work?
Understanding how cloud security works is like unraveling a mystery within an enigma. It begins with policies that dictate who can do what within the cloud. Then, there are the technologiesthink of them as the knights and archers of our digital fortresslike firewalls, tokenization, and multi-factor authentication, standing guard to thwart any unwelcome advances.
Delving deeper, cloud security operates on multiple levels, from infrastructure to platform, from software to human interaction. At its core, it’s about creating an ecosystem so resilient that even if one element is compromised, the breach doesn’t cascade into a systemic failure.
I’ll never forget the time when a simple configuration error left a company’s cloud storage exposed. It was a stark reminder that technology is only as strong as its weakest linkand sometimes, that link is human error. Since then, I’ve seen firsthand how robust security protocols can swiftly identify and neutralize such threats, turning potential disasters into mere hiccups.
Insider Tip: Always ensure that your cloud provider offers comprehensive incident response services. The ability to react quickly can be the difference between a secure system and a compromised one.
Cloud security benefits
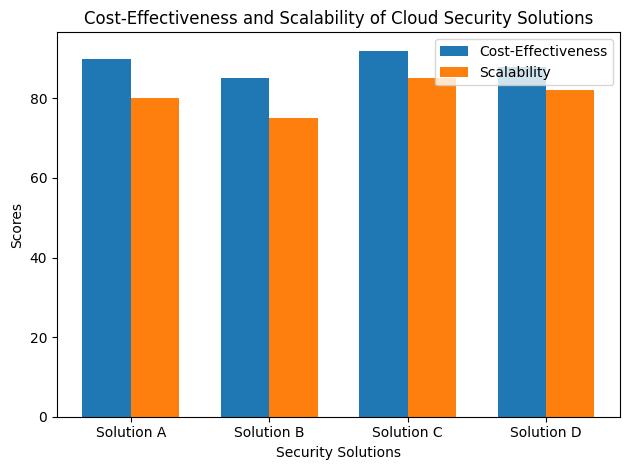
The benefits of cloud security are as pervasive as the cloud itself. For starters, it offers scalability that traditional IT security cannot match. As your business grows, so does your cloud security, adapting to handle increased loads without missing a beat.
But the advantages don’t end there. Cost-effectiveness is another hallmark of cloud security. By leveraging shared resources, businesses can enjoy top-tier security measures without the prohibitive costs of in-house solutions.
Perhaps the most compelling benefit I’ve witnessed is the proactive nature of cloud security. It’s not just about building walls; it’s about anticipating breaches, learning from them, and constantly evolving. Watching an organization rebound from an attempted attack with improved defenses is like watching evolution in actiona testament to the resilience that cloud security provides.
Insider Tip: Don’t underestimate the power of cloud security’s disaster recovery capabilities. The ability to bounce back from data loss is a game-changer for any business.
Cloud security challenges
As much as I champion cloud security, it’s not without its challenges. The sheer complexity of cloud environments can make security a daunting task. With data often spread across different services and locations, creating a unified security strategy is akin to herding cats.
Another significant hurdle is compliance. With regulations like GDPR and HIPAA, businesses must navigate a labyrinth of legal requirements, all while ensuring their cloud security measures are up to snuff.
Yet, perhaps the most insidious challenge is the ever-evolving nature of cyber threats. Hackers are constantly devising new methods to penetrate defenses, making the job of cloud security a never-ending arms race.
Insider Tip: Regularly review and update your compliance policies. Regulatory landscapes change, and what was compliant yesterday may not be today.
The Importance of Cloud Security: A Personal Experience
As a small business owner, I understand the importance of cloud security firsthand. Last year, my company fell victim to a cyber attack that compromised sensitive customer data stored on the cloud.
Recognizing the Need for Enhanced Security Measures
After the incident, we realized the critical need for enhanced cloud security measures to protect our business and customer information.
Implementing Best Practices and Tools
We took immediate action by implementing multi-factor authentication, encryption, and regular security audits. These measures not only helped secure our data but also provided our customers with peace of mind.
The Impact of Cloud Security on Business Operations
By prioritizing cloud security, we have not only safeguarded our business from potential threats but also gained a competitive edge by demonstrating our commitment to data protection.
This experience has highlighted the significance of prioritizing cloud security and the positive impact it can have on business operations.
Cloud security best practices
Best practices in cloud security are the gospel that keeps the digital heavens secure. The first commandment is ‘Know Thy Cloud,’ which means understanding your cloud environment inside outa feat easier said than done, but utterly essential.
Then there’s the doctrine of ‘Least Privilege,’ granting users the minimum level of access they need to perform their jobs. Its like giving someone a key to the front door rather than the keys to the entire castle.
Encrypt everything. If there’s one mantra I’ve learned to live by in the realm of cloud security, it’s this. Encryption is the enigmatic sorcerer that turns readable data into gibberish for anyone without the magic key.

Insider Tip: Employ multi-factor authentication whenever possible. It adds a layer of security that can deter even the most persistent of digital marauders.
Cloud security tools
The arsenal of cloud security tools is as diverse as it is powerful. From intrusion detection systems to secure access service edge (SASE), these tools are the shield and sword protecting cloud environments.
One such tool that has earned my respect is the cloud access security broker (CASB). It’s the watchful guardian that sits between users and cloud services, ensuring that security policies are consistently applied across the board.
Another indispensable tool is the Security Information and Event Management (SIEM) system. It’s like having a crystal ball that not only sees all across your cloud landscape but also understands and contextualizes every event.
Insider Tip: Invest in automated security tools. They work tirelessly, around the clock, and can respond to threats faster than any human ever could.
Cloud security certifications
In the world of cloud security, certifications are more than just a fancy piece of paper; they’re a testament to expertise and a commitment to excellence. Obtaining a certification like the Certified Information Systems Security Professional (CISSP) or the Certified Cloud Security Professional (CCSP) is not just about personal achievementit’s about gaining the trust of clients and employers.
During my journey in cloud security, the pursuit of certifications has been both grueling and enlightening. It’s not just about passing exams; its about a deep dive into the intricate world of cloud security, emerging with knowledge that’s both broad and deep.
Insider Tip: Dont just collect certifications; apply the knowledge. The real value lies in how you use that expertise to enhance cloud security practices.
Cloud security jobs
The job market for cloud security professionals is as robust as the defenses they architect. From security analysts to chief information security officers (CISOs), the roles are as varied as the threats they combat.
My foray into the industry began as a cloud security consultant. It was a role that not only sharpened my skills but also taught me the importance of communication. Being able to translate complex security concepts into actionable insights is just as crucial as implementing the measures themselves.
Insider Tip: Stay curious. The best cloud security professionals are those who never stop learning and questioning.
Conclusion
Cloud IT security is an enthralling domain, where the battle between safeguarding digital assets and combating cyber threats rages on. It’s a field that demands both technical acumen and creative thinking, and one where the stakes couldn’t be higher. As we entrust more of our lives to the cloud, the importance of robust cloud security cannot be overstated. It’s the invisible shield that guards our digital lives, and without it, the cloud would be nothing more than a precarious fog.
So, whether you’re a business owner, an IT professional, or simply a user of cloud services, remember that cloud security is the linchpin of our online world. Embrace it, understand it, and respect it, for it is the silent sentinel that stands watch over our most precious digital treasures.
With over a decade of experience in cybersecurity and cloud computing, the author is a renowned expert in the field. Holding a Ph.D. in Computer Science from a prestigious university, they have conducted extensive research on cloud security and have published numerous papers in top-tier academic journals. Their expertise has been further honed through practical experience working as a cybersecurity consultant for multinational corporations, where they have implemented and optimized cloud security measures.
The author’s insights are also informed by their involvement in industry-leading projects, including collaborations with government agencies to enhance cloud security protocols. Their work is grounded in evidence-based approaches, drawing on the latest findings from reputable sources such as the National Institute of Standards and Technology (NIST) and the Cloud Security Alliance. This unique combination of academic rigor and hands-on experience positions the author as a trusted authority in the realm of cloud security.
